In this blog post, we are going to install a WireGuard server on Linux. I already showed you a WireGuard installation on Amazon Lightsail in a previous blog post. And in this past blog post, I showed you the WireGuard client installation on Windows. The issue with the installation in these blog posts is that it only supports IPv4. If you have a client that only uses IPv6, the described configuration will not work. The problem is that Amazon Lightsail currently does not support IPv6.
This time, we will perform a WireGuard server installation that supports both IPv4 and IPv6 peers. For this installation, I am using a Virtual Private Server from Hetzner (referral link), a company that runs data centers in Germany (Nuremberg, Falkenstein), Finland (Helsinki), and in the US (Ashburn, VA). The servers from Hetzner have both IPv4 and IPv6 support.
I am running the following installation on a fresh Ubuntu 20.04 server with an SSH server and the base system installed. I rented the smallest server (CX11) that Hetzner offers with 2 GB RAM. This is plenty of memory for just running a WireGuard server. This virtual server costs 3.76 Euros per month (December 2021).
For this WireGuard installation, I'm going to use a script hosted in this GitHub repository.
First, a word of warning: When you download scripts from the internet,
do not execute them. Always open the file in an editor after you have downloaded it.
Then, scan the code and try to understand what the script does. Look for statements
like apt, rpm, yum, wget, and curl that download files from the internet. The reason to be careful
is that it's straightforward for an attacker to install a backdoor or malware on your server this way.
With this warning out of the way, we can proceed with the installation.
The benefit of using this batch file is that it supports multiple Linux distributions:
CentOS, Debian, Ubuntu, Arch, Fedora, Redhat, Raspbian, PopOS, Manjaro, and Kali.
The installation requires a Linux system with a 3.1 or newer kernel. To execute the script, you also need root access or a user account with sudo privileges.
Installation ¶
Make sure that your system is up to date. On Ubuntu, you can do this with the following command:
apt update
apt full-upgrade
Download the latest version of the script:
curl https://raw.githubusercontent.com/complexorganizations/wireguard-manager/main/wireguard-manager.sh --create-dirs -o /usr/local/bin/wireguard-manager.sh
Open the script in an editor and check the contents!
Next, execute the script with the following command:
bash /usr/local/bin/wireguard-manager.sh
The script will guide you through the installation.
Firstly, the script asks you about the IP addresses and which tools to use to detect the external IP addresses.
The recommended settings should work fine. However, when I ran this script, the external IP address detection with curl did not work. I had to select option 2 (Custom) for both IPv4 and IPv6. The custom option allows you to enter the external IP addresses manually.
What IPv4 subnet do you want to use?
1) 10.0.0.0/8 (Recommended)
2) Custom (Advanced)
Subnet Choice [1-2]:1
What IPv6 subnet do you want to use?
1) fd00:00:00::0/8 (Recommended)
2) Custom (Advanced)
Subnet Choice [1-2]:1
How would you like to detect IPv4?
1) Curl (Recommended)
2) Custom (Advanced)
IPv4 Choice [1-2]:2
Custom IPv4:65.21.176.63
How would you like to detect IPv6?
1) Curl (Recommended)
2) Custom (Advanced)
IPv6 Choice [1-2]:2
Custom IPv6:2a01:4f9:c010:574c::/64
How would you like to detect NIC?
1) IP (Recommended)
2) Custom (Advanced)
Nic Choice [1-2]:1
Next, it asks you about the port you want WireGuard to listen on. I recommend using a custom port (option 2). For this example, I set the port to 55334.
What port do you want WireGuard server to listen to?
1) 51820 (Recommended)
2) Custom (Advanced)
Port Choice [1-2]:2
Custom port [1-65535]:55334
Using a custom or random port compared to the predefined 51820 port does not increase security, but it prevents a few drive-by port scans that only listen for well-known ports. A targeted attack against your server with a full port scan will reveal all open ports.
Next, the script asks about the keepalive interval and MTU. I recommend you confirm the defaults.
What do you want your keepalive interval to be?
1) 25 (Default)
2) Custom (Advanced)
Nat Choice [1-2]:1
What MTU do you want to use?
1) 1280 (Recommended)
2) Custom (Advanced)
MTU Choice [1-2]:1
After that, the script asks you what IP version your clients should use to connect to the WireGuard server. Here, I would always choose option 1 unless all your clients only use IPv6 and not IPv4 addresses.
What IP do you want to use to connect to the WireGuard server?
1) IPv4 (Recommended)
2) IPv6
IP Choice [1-2]:1
Next, you can disable one of the IP protocols. This is useful if you are sure that you are only going to use one of the IP protocols, but usually, you would select option 1.
Do you want to disable IPv4 or IPv6 on the server?
1) No (Recommended)
2) Disable IPv4
3) Disable IPv6
Disable Host Choice [1-3]:1
The next option concerns the client. The script asks you if the client should forward all traffic through the VPN connection or exclude private IPs. Private IP addresses are located in these ranges: 192.168.0.0–192.168.255.255, 172.16.0.0–172.31.255.255, and 10.0.0.0–10.255.255.255. These are used for internal LANs. If you use a WireGuard connection and, at the same time, want to connect to your LAN, select option 2. In this example, all my clients are not connected to a LAN, so I select option 1.
What traffic do you want the client to forward through WireGuard?
1) Everything (Recommended)
2) Custom (Advanced)
Client Allowed IP Choice [1-2]:1
The next question is about installing real-time updates and setting up a backup. Select the recommended options.
Would you like to setup real-time updates?
1) Yes (Recommended)
2) No (Advanced)
Automatic Updates [1-2]:1
Would you like to setup real-time backup?
1) Yes (Recommended)
2) No (Advanced)
Automatic Backup [1-2]:1
Next, the script asks you about installing a DNS server. Your WireGuard server can act as a DNS resolver. In this setup, all DNS requests from the clients are routed through the VPN and are hidden from the ISP. If you select the recommended option, the script will install Unbound. Additionally, you can also install ad and malware blockers.
Which DNS provider would you like to use?
1) Unbound (Recommended)
2) Custom (Advanced)
DNS provider [1-2]:1
Do you want to prevent advertisements, tracking, malware, and phishing using the content-blocker?
1) Yes (Recommended)
2) No
Content Blocker Choice [1-2]:1
The script now asks about a name for the first client configuration. Here, I name it "client1."
Let's name the WireGuard Peer. Use one word only, no special characters, no spaces.
Client name:client1
And lastly, the script asks you if you want to expire the clients after a certain period.
Would you like to expire the peer after a certain period of time?
1) Every Year (Recommended)
2) No
Automatic config expire [1-2]:1
After this, the script starts to install WireGuard and all dependent libraries. The last step creates the client configuration and displays a QR code on the screen. You can scan this code with your iOS and Android WireGuard app.
The script writes the server configuration into the file /etc/wireguard/wg0.conf
and the client configuration into the file /etc/wireguard/clients/client1-wg0.conf.
Remember to open the incoming WireGuard port if a firewall is installed on the server. You only have to open the port for UDP connections. When the server runs the UFW firewall, you open the port with the following command:
ufw allow 55334/UDP
Adding more clients ¶
The script is not only useful for the initial installation; it can also help you create more client configurations. When you run the script a second time, it recognizes that a WireGuard server is already installed and presents a different menu.
bash /usr/local/bin/wireguard-manager.sh
What do you want to do?
1) Show WireGuard
2) Start WireGuard
3) Stop WireGuard
4) Restart WireGuard
5) Add WireGuard Peer (client)
6) Remove WireGuard Peer (client)
7) Reinstall WireGuard
8) Uninstall WireGuard
9) Update this script
10) Backup WireGuard
11) Restore WireGuard
12) Update Interface IP
13) Update Interface Port
14) Purge WireGuard Peers
15) Generate QR Code
Here you can start and stop the WireGuard server, add and remove WireGuard clients, and uninstall the WireGuard server.
To add a new client, select option 5 and give the client a name.
Select an Option [1-15]:5
Let's name the WireGuard Peer. Use one word only, no special characters, no spaces.
New client peer:client2
The script displays the QR code and creates a new configuration file in the /etc/wireguard/clients/ folder.
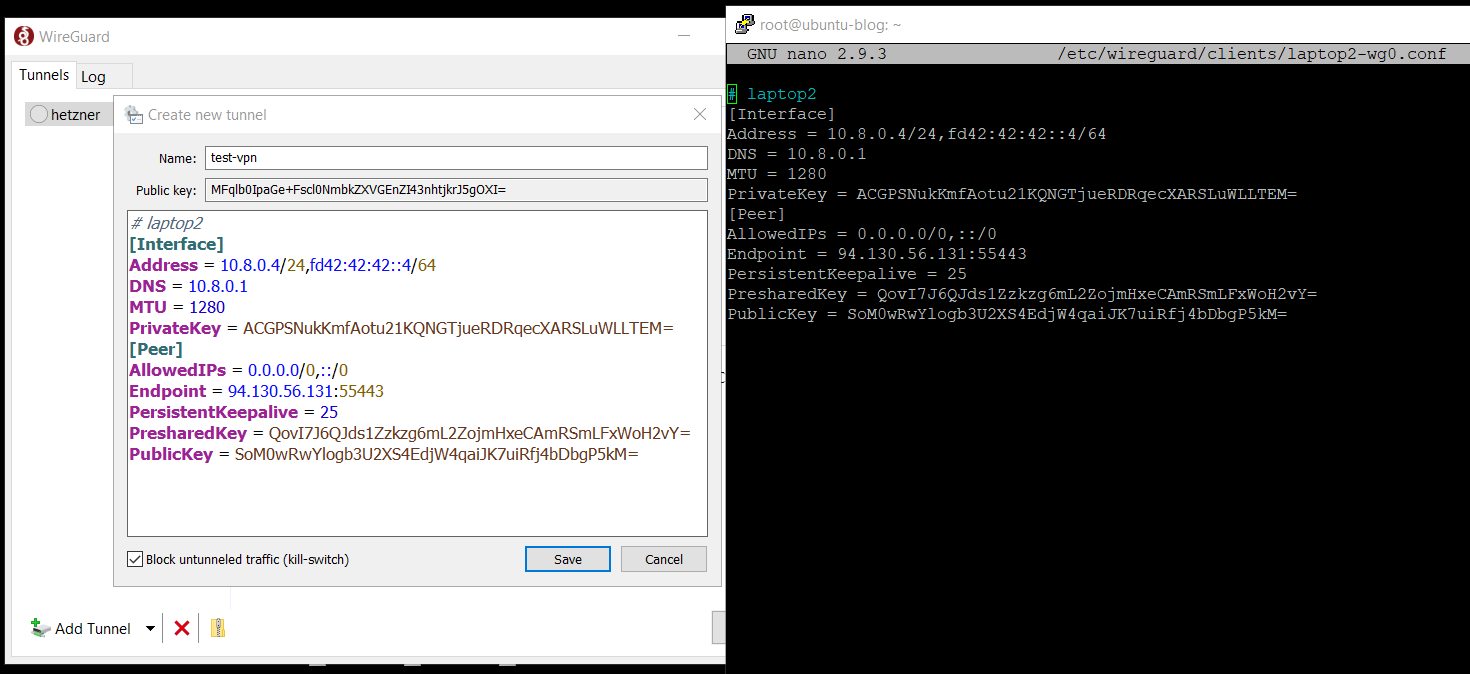
When you have a client that can't scan the QR code, like the Windows client, open the configuration file on the server:
cat /etc/wireguard/clients/client2-wg0.conf
Open the configuration dialog on the client and copy and paste the configuration from the server into your client.
Installing WireGuard with the script from complexorganizations is very convenient. You get a well-tested server configuration that is reviewed and used by many users.